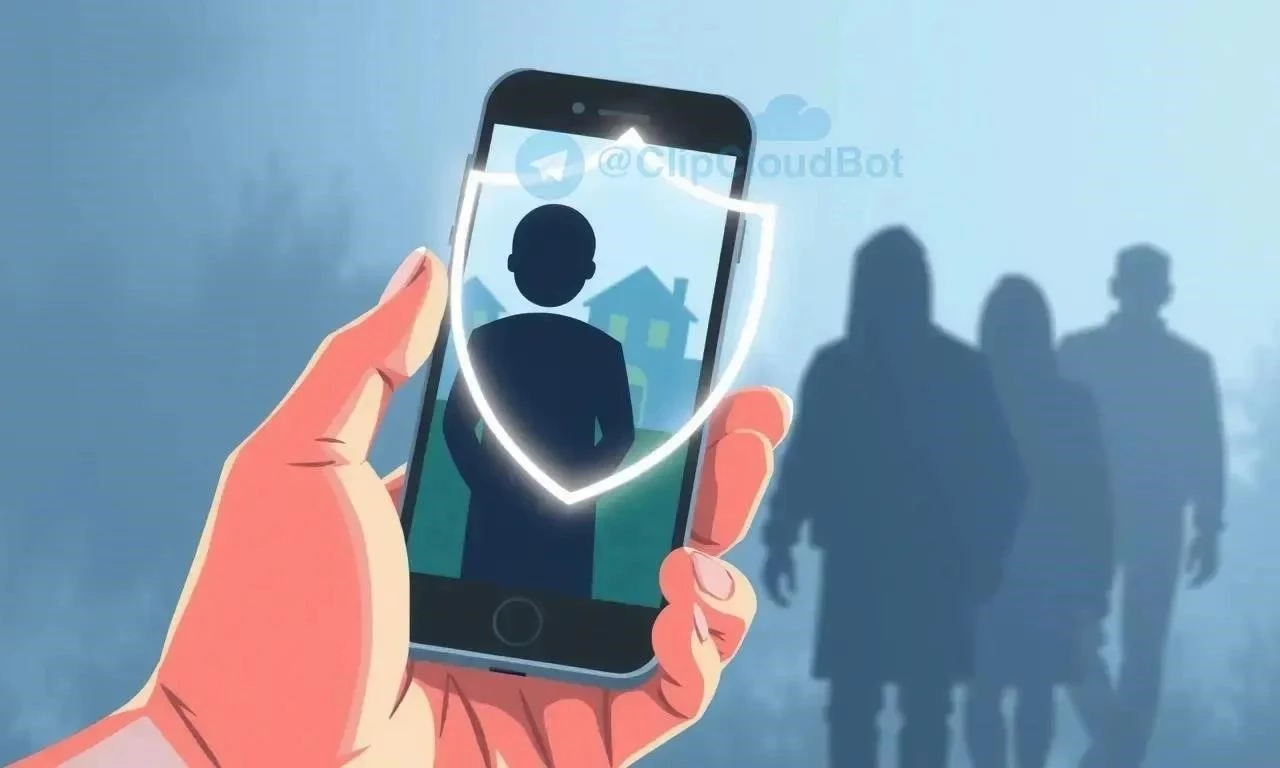
The digital age has ushered in unprecedented connectivity and convenience, transforming nearly every facet of our lives. However, this technological revolution presents a complex paradox when it comes to domestic violence. While technology can empower victims with tools for seeking help and documenting abuse, it also provides perpetrators with new avenues for control, harassment, and surveillance. This article delves into the intricate ways technology acts as both a weapon and a shield in the context of domestic violence, exploring its potential benefits and inherent risks.
The Dark Side: Technology as a Weapon
Unfortunately, technology’s accessibility makes it a powerful tool for abusers. Here are some ways technology is used to perpetrate abuse:
- Cyberstalking: Tracking location, monitoring online activity, and impersonating victims online.
- Harassment: Sending abusive messages, posting demeaning content, and spreading false information.
- Control: Demanding access to passwords, monitoring phone calls and emails, and using smart home devices to manipulate the environment.
- Isolation: Limiting access to online resources and social media, cutting off victims from their support networks.
Specific Examples of Tech-Enabled Abuse
- GPS Tracking: Abusers use location tracking apps to monitor their partner’s movements.
- Social Media Monitoring: Constant surveillance of social media accounts to scrutinize interactions and control online presence.
- Smart Home Manipulation: Controlling lights, temperature, and security systems to intimidate or control.
- Deepfakes and Online Impersonation: Creating fake accounts and spreading misinformation to damage a victim’s reputation.
The Light Side: Technology as a Shield
Despite the risks, technology can also be a lifeline for victims of domestic violence. It provides tools for safety, communication, and evidence gathering.
Technology can empower victims by:
- Providing avenues for communication: Secretly contacting support networks and emergency services.
- Documenting abuse: Recording evidence of abuse through photos, videos, and screenshots.
- Accessing resources: Finding information about shelters, legal aid, and counseling services.
- Enhancing safety: Using safety apps and emergency contacts to alert trusted individuals in dangerous situations.
Comparative Analysis: Tools for Abuse vs. Tools for Safety
| Feature | Technology as a Weapon | Technology as a Shield |
|---|---|---|
| Communication | Abusive texts, online harassment, impersonation | Secret communication with support networks, contacting emergency services |
| Surveillance | GPS tracking, monitoring online activity, accessing personal accounts | Documenting abuse with photos and videos, collecting evidence |
| Control | Demanding passwords, controlling smart home devices, limiting access to resources | Finding information about shelters, legal aid, and counseling |
| Privacy | Violating privacy through spyware and hacking | Using encrypted messaging apps, protecting online identity |
FAQ: Technology and Domestic Violence
What is tech abuse?
Tech abuse refers to the use of technology to control, harass, stalk, or intimidate a partner or family member. It encompasses a wide range of behaviors, from monitoring online activity to using smart home devices to manipulate the environment.
How can I protect myself from tech abuse?
There are several steps you can take, including strengthening your passwords, reviewing your privacy settings on social media, and being aware of the apps and devices your partner has access to. It’s also important to seek help from domestic violence organizations and law enforcement if you are experiencing tech abuse.
What resources are available for victims of tech abuse?
Many organizations offer support and resources for victims of tech abuse, including the National Domestic Violence Hotline, the National Network to End Domestic Violence, and local domestic violence shelters. These organizations can provide safety planning, legal assistance, and counseling services.
How can I document tech abuse?
Take screenshots of abusive messages, save emails, and record videos or audio recordings of incidents. Keep a log of all instances of tech abuse, including the date, time, and specific details. This documentation can be valuable evidence in legal proceedings.
What should I do if I think my device has been compromised?
If you suspect your device has been compromised, consider contacting a professional to scan it for malware and spyware. You may also want to change your passwords on all of your accounts and consider getting a new device.
The digital age has ushered in unprecedented connectivity and convenience, transforming nearly every facet of our lives. However, this technological revolution presents a complex paradox when it comes to domestic violence. While technology can empower victims with tools for seeking help and documenting abuse, it also provides perpetrators with new avenues for control, harassment, and surveillance. This article delves into the intricate ways technology acts as both a weapon and a shield in the context of domestic violence, exploring its potential benefits and inherent risks;
Unfortunately, technology’s accessibility makes it a powerful tool for abusers. Here are some ways technology is used to perpetrate abuse:
- Cyberstalking: Tracking location, monitoring online activity, and impersonating victims online.
- Harassment: Sending abusive messages, posting demeaning content, and spreading false information.
- Control: Demanding access to passwords, monitoring phone calls and emails, and using smart home devices to manipulate the environment.
- Isolation: Limiting access to online resources and social media, cutting off victims from their support networks.
- GPS Tracking: Abusers use location tracking apps to monitor their partner’s movements.
- Social Media Monitoring: Constant surveillance of social media accounts to scrutinize interactions and control online presence.
- Smart Home Manipulation: Controlling lights, temperature, and security systems to intimidate or control.
- Deepfakes and Online Impersonation: Creating fake accounts and spreading misinformation to damage a victim’s reputation.
Despite the risks, technology can also be a lifeline for victims of domestic violence. It provides tools for safety, communication, and evidence gathering.
Technology can empower victims by:
- Providing avenues for communication: Secretly contacting support networks and emergency services.
- Documenting abuse: Recording evidence of abuse through photos, videos, and screenshots.
- Accessing resources: Finding information about shelters, legal aid, and counseling services;
- Enhancing safety: Using safety apps and emergency contacts to alert trusted individuals in dangerous situations.
| Feature | Technology as a Weapon | Technology as a Shield |
|---|---|---|
| Communication | Abusive texts, online harassment, impersonation | Secret communication with support networks, contacting emergency services |
| Surveillance | GPS tracking, monitoring online activity, accessing personal accounts | Documenting abuse with photos and videos, collecting evidence |
| Control | Demanding passwords, controlling smart home devices, limiting access to resources | Finding information about shelters, legal aid, and counseling |
| Privacy | Violating privacy through spyware and hacking | Using encrypted messaging apps, protecting online identity |
Tech abuse refers to the use of technology to control, harass, stalk, or intimidate a partner or family member. It encompasses a wide range of behaviors, from monitoring online activity to using smart home devices to manipulate the environment.
There are several steps you can take, including strengthening your passwords, reviewing your privacy settings on social media, and being aware of the apps and devices your partner has access to. It’s also important to seek help from domestic violence organizations and law enforcement if you are experiencing tech abuse.
Many organizations offer support and resources for victims of tech abuse, including the National Domestic Violence Hotline, the National Network to End Domestic Violence, and local domestic violence shelters. These organizations can provide safety planning, legal assistance, and counseling services.
Take screenshots of abusive messages, save emails, and record videos or audio recordings of incidents. Keep a log of all instances of tech abuse, including the date, time, and specific details. This documentation can be valuable evidence in legal proceedings.
If you suspect your device has been compromised, consider contacting a professional to scan it for malware and spyware. You may also want to change your passwords on all of your accounts and consider getting a new device.
My Personal Experience with Tech Safety
After researching and learning about the potential for technology to be used in domestic violence situations, I decided to take a proactive approach to my own digital security. I’m not a victim of domestic violence, thankfully, but I wanted to understand how vulnerable I might be. I started by going through all my social media accounts and tightening up my privacy settings. It was actually quite shocking to see how much information I was sharing publicly without even realizing it. I changed all my passwords to be much stronger, using a password manager to help me keep track of them. I even enabled two-factor authentication on everything I could.
Then I decided to experiment a bit. I downloaded a free GPS tracking app on my phone, just to see how easily someone could track my location. I gave “Mark,” a fictional character I created for this experiment, access to the app. I was honestly unnerved by how precisely it tracked my movements. It really drove home the point that if someone wanted to, they could easily monitor me without my knowledge. I immediately deleted the app afterwards.
Next, I explored some of the safety apps designed for domestic violence victims. I found an app called “Noonlight,” which allows you to quickly alert emergency services with just a press of a button. I tested it out (without actually calling emergency services, of course!) and was impressed by how quickly it connected me to a dispatcher. It made me feel a little safer knowing that such a tool exists. I also downloaded an encrypted messaging app, Signal, and started using it to communicate with some of my close friends. It’s reassuring to know that our conversations are more secure.
Finally, I spent some time thinking about my smart home devices. I have a smart thermostat and a few smart lights, all connected to my Wi-Fi network. I realized that if someone gained access to my account, they could potentially control these devices and use them to harass or intimidate me. So, I changed the password on my Wi-Fi network and made sure to enable two-factor authentication on my smart home accounts. I also renamed all my devices to more generic names, so it wouldn’t be obvious what they were. For example, instead of “Living Room Lights,” I renamed it “Lamp 1.” It might seem like a small thing, but it’s an extra layer of security.
The whole experience was eye-opening. I realized that while technology can be a great tool, it’s also important to be aware of the risks and take steps to protect yourself. Even though I’m not personally experiencing domestic violence, I feel much more prepared and informed now. And I hope that by sharing my experience, I can help others stay safe as well.